Authentication & Security
Secure access control and authentication mechanisms for the Blueberry IDP platform.
Overview
Blueberry IDP implements a comprehensive security model using Firebase Authentication for user management, API tokens for programmatic access, and role-based access control (RBAC) for fine-grained permissions.
Authentication Flow
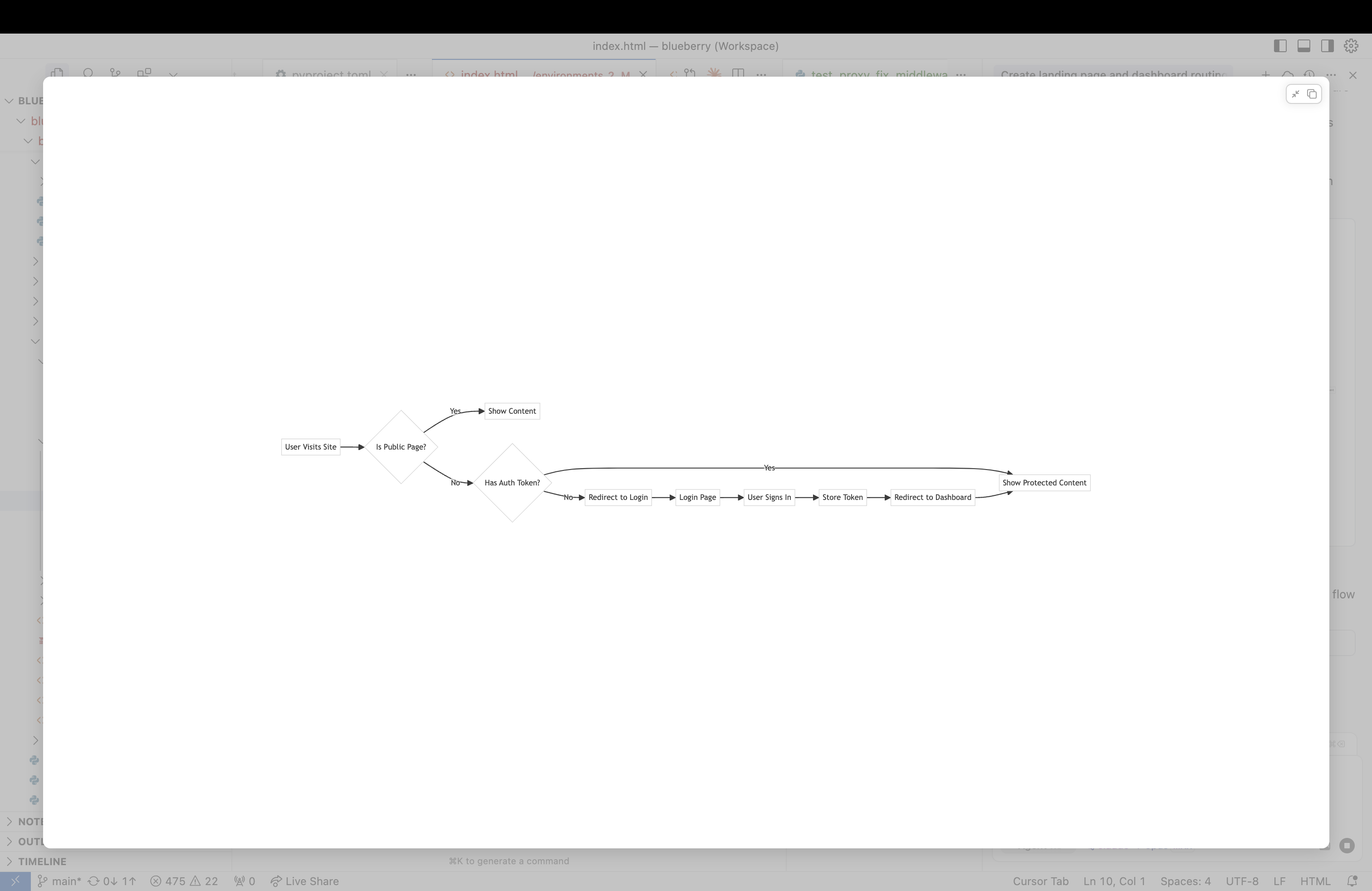
Blueberry IDP uses Firebase Authentication with support for both internal and external users, providing seamless integration with existing identity providers.
User Authentication
- Firebase Auth: Primary authentication provider
- Email/Password: Direct user registration and login
- OAuth Providers: Google, GitHub, and other providers
- Session Management: JWT tokens with automatic refresh
API Authentication
- API Tokens: Long-lived tokens for CI/CD integration
- Bearer Authentication: Standard HTTP Authorization header
- Scoped Access: Environment-specific permissions
- Token Rotation: Manual and automatic token renewal
Security Features
Access Control
- Role-based access control (RBAC)
- Resource-level permissions
- Environment isolation
- Audit logging for all actions
Infrastructure Security
- Kubernetes namespace isolation
- Network policies for pod-to-pod communication
- Secret management via Kubernetes secrets
- TLS encryption for all external traffic
Configuration
Firebase Setup
The platform uses Firebase Authentication with the following configuration:
# Environment variables
FIREBASE_PROJECT_ID=your-project-id
FIREBASE_WEB_API_KEY=your-api-key
FIREBASE_AUTH_DOMAIN=your-project.firebaseapp.com
# Supported providers
- Email/Password authentication
- Google OAuth
- GitHub OAuth (optional)
- Custom SAML providers (enterprise)API Token Management
API tokens provide programmatic access for CI/CD pipelines and automation:
# Create a new API token
curl -X POST https://blueberry.florenciacomuzzi.com/api/tokens \
-H "Authorization: Bearer $USER_TOKEN" \
-H "Content-Type: application/json" \
-d '{
"name": "CI Pipeline Token",
"description": "Token for automated environment creation",
"scopes": ["environments:create", "environments:read"]
}'
# Use token in API requests
curl -H "Authorization: Bearer $API_TOKEN" \
https://blueberry.florenciacomuzzi.com/api/environmentsSecurity Best Practices
For Users
- Enable two-factor authentication (2FA)
- Use strong, unique passwords
- Regularly review API token usage
- Report suspicious activity immediately
For Administrators
- Regularly rotate API tokens
- Monitor audit logs for anomalies
- Implement principle of least privilege
- Keep Firebase SDK and dependencies updated
Common Security Scenarios
🔐 CI/CD Pipeline Access
For automated environment creation in CI/CD pipelines:
- Create a dedicated API token with minimal required scopes
- Store the token securely in your CI/CD platform's secret management
- Set appropriate token expiration based on usage patterns
- Monitor token usage and rotate regularly
👥 Team Access Management
For managing team access to environments:
- Use Firebase user management for team member accounts
- Implement environment-level access controls
- Regular review of user permissions and access levels
- Audit logs for tracking environment access and modifications
🚨 Security Incident Response
In case of suspected security incidents:
- Immediately revoke suspected compromised API tokens
- Review audit logs for unauthorized access patterns
- Check environment creation and deletion patterns
- Contact the platform team for assistance if needed
Related Documentation
📚 Architecture
🔧 Operations
Security is continuously improved. Report security issues to the platform team immediately.